In the security world, a zero-day marks the start of a race. A zero-day vulnerability is a newly discovered flaw, usually a bug, that attackers can exploit before defenders have time to respond. As soon as a CVE (Common Vulnerabilities and Exposures) is published, it sets off an urgent chain reaction. The announcement typically includes a description of the vulnerability, its severity, and a list of affected versions. In many cases, a patch is also released. That’s when security teams scramble to update packages, rebuild images, and deploy fixed versions into production.
There are plenty of tools that can tell you at build time whether you’ve included a vulnerable package in an image. But there are limits to what build-time tooling can tell you. It can’t tell you if the affected code is actually running in production. It can’t tell you whether someone is actively exploiting it. And it certainly can’t tell you how that vulnerability might be behaving in the wild. This lack of visibility means teams often have to guess how urgently they need to respond, or worse, remain unaware of compromise until it’s too late.
This is exactly the problem that Tetragon solves.
Tetragon: Real-Time Insight from Inside the Kernel
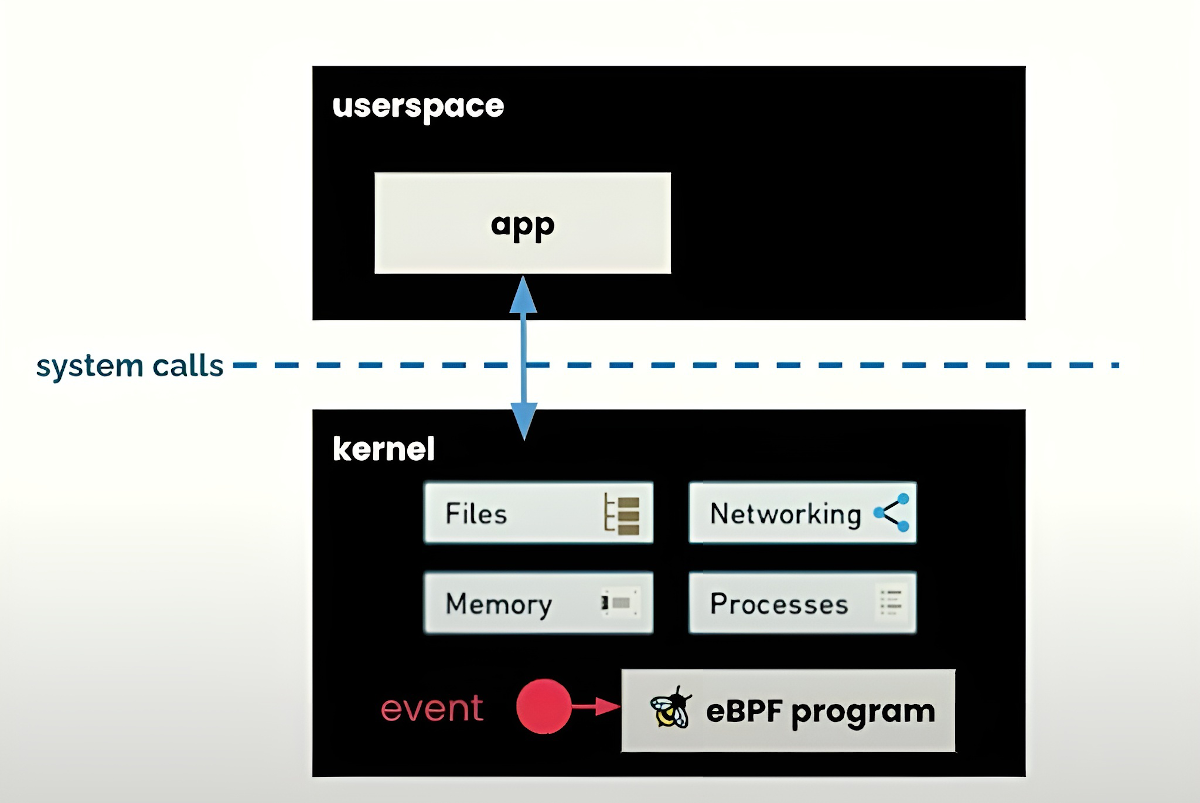
Tetragon is the newest member of the Cilium project family (which also includes Hubble). It’s an open-source, eBPF-based security observability tool built for detecting and mitigating threats as they happen. Unlike static scanners or user-space agents, Tetragon hooks directly into kernel-level events using eBPF, giving it visibility and control without the overhead of traditional monitoring tools.
Tetragon gives you detailed runtime visibility and lets you observe events including: process execution and exit, file access, parent/child hierarchy, network destinations, privilege changes, and more. But the real power lies in Tetragon’s policies, which let you specify exactly what you want to observe (or block). It might be access to a sensitive file, a privilege escalation attempt, a network connection to a suspicious IP, or - critically - behavior associated with a known vulnerability. These policies don’t just generate alerts. They can also block execution in real time, right from within the kernel.
The 2024 XZ Utils Backdoor
One of the most alarming zero-days in recent memory involved XZ Utils, a core compression library. A bad actor spent over two years gaining trust in the project, becoming a maintainer, and eventually committing code that added a remote code execution backdoor to versions 5.6.0 and 5.6.1.
That meant anyone using those versions, especially in combination with SSH, could be compromised.
With Tetragon, defenders would have a powerful way to respond. A policy could be written to watch for the sshd process loading those specific vulnerable versions of liblzma.so. If detected, Tetragon would emit a rich event log showing what happened, including the process involved, the command executed, and the context in which it occurred. And if configured, Tetragon could go a step further, killing the process before the exploit could complete. Watch the live demo to see Tetragon neutralizing this exploit attempt.
Performance Without Compromise
This kind of real-time security observability might sound expensive in terms of system performance. However, surprisingly, it’s not. Tetragon uses eBPF to evaluate policies inside the kernel itself, without shipping all events to user space for filtering. This in-kernel filtering is what makes it both powerful and lightweight.
In benchmarks, Tetragon introduced less than 2% overhead when monitoring over 1.5 million file-read events during a kernel build. In another test involving high volumes of multi-threaded file access, the overhead was around 0.2%. Compared to traditional security agents that stream everything to user space, this is a massive efficiency win. Tetragon gives you detailed observability at scale without sacrificing performance.
Final Thoughts
Responding to zero-day vulnerabilities is hard. Patching quickly is important, but knowing what’s already running and what’s already been exploited is critical. Tetragon gives you a fighting chance by making runtime behavior observable, actionable, and when needed, stoppable.
It’s quick to deploy, runs with minimal overhead, and gives security teams the confidence that they’re not operating in the dark. As Jason Cetina, a security expert at GitHub, put it:
“Tetragon provides security teams with rich data that connects network, process, and Kubernetes metadata into event records. (…) It’s quick to set up, has minimal overhead, and is critical when you’re running at scale.”
Read the full quote in this article.
If you want to see what’s happening under the hood of your system, not just what went into it, Tetragon is well worth a look.
Try Tetragon now: github.com/cilium/tetragon
Explore example policies: xz-utils detection template

